The threat landscape is evolving, and staying ahead of it is crucial for any security team. In Cisco’s latest report, Cyber Threat Trends Report: From Trojan Takeovers to Ransomware Roulette, the company delves into how monitoring network traffic can help organisations defend against ever-shifting cyber threats.
Monitoring DNS activity is a particularly effective way to detect malicious behaviour. In today’s environment, almost every cyber attack relies on an internet connection. For example, backdoors require a connection to send instructions to compromised systems, while ransomware groups need to remotely activate encryption on a victim’s systems. Cisco’s report highlights the extraordinary volume of malicious domains that must be blocked—over one million every hour—showing just how critical DNS-layer security has become.
Understanding the Data
To make sense of the vast amount of data, Cisco analysed the categories that Umbrella applies to known malicious domains. Over an eight-month period from August 2023 to March 2024, the company tracked the average monthly volume of each threat category. By comparing these volumes against the overall average, they identified key trends in cyber threats.
Patterns emerged that offer valuable insights into the most active threat types.
Information Stealers
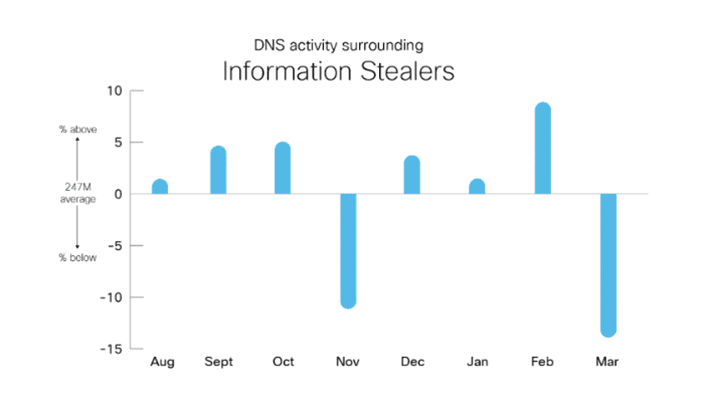


Information stealers topped the list as the most active threat category during the time frame. Given that this category involves exfiltrating large amounts of data and monitoring communications, the high level of activity was anticipated. A clear pattern was observed: three months of above-average activity followed by a month of reduced activity, likely due to attackers processing the data they’ve stolen.
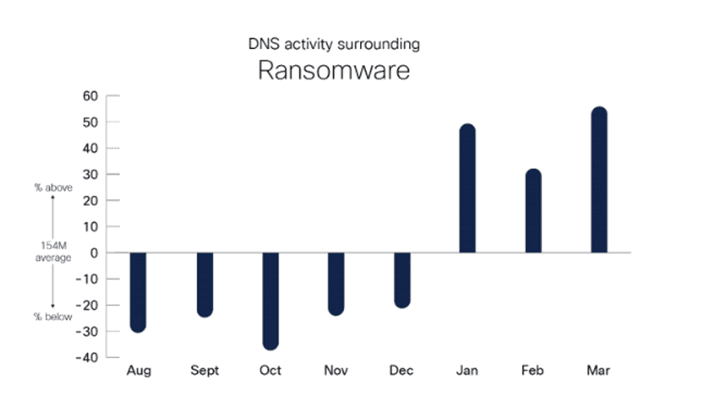
Trojans vs Ransomware
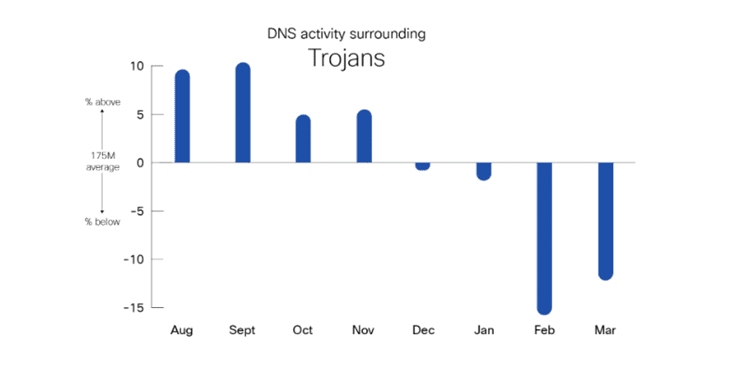


A comparison of Trojan and ransomware activity revealed contrasting trends. Trojan activity was initially high but declined over time, a fluctuation that reflects the cyclical nature of the threat landscape. Meanwhile, ransomware activity increased significantly from January onwards, suggesting a shift in tactics. Often, attackers use Trojans to gain control of a network before deploying ransomware to maximise damage.
These findings are just a snapshot of the trends covered in Cisco’s comprehensive report, which also includes additional threat categories following similar patterns.
How to Protect and Monitor Your Network Traffic


Given the centrality of internet connections in modern cyber threats, controlling and monitoring DNS queries is a powerful way to block malicious traffic. Cisco’s report recommends several strategies, including:
- Leveraging DNS Security – Using DNS-layer security to block threats before they reach end-user devices.
- Protecting Endpoints – Ensuring all devices are secure to prevent network breaches.
- Implementing a Comprehensive Defence Strategy – Adopting a layered security approach to protect against a wide range of threats.
With over 30,000 customers relying on Cisco’s DNS-layer security, the company’s tools like Umbrella and Secure Access are proving to be effective in protecting organisations across various environments.
For more detailed insights, download the full report: Cyber Threat Trends Report: From Trojan Takeovers to Ransomware Roulette.